- Level 6 Unit T/615/2726 Assignment: Strategic Project Management: Identifying, Planning, and Controlling Projects for Business Success
- EDD-U1-T4 Assignment: Internal and External Support Services for Educational Practitioners
- Discussion Paper on Market Forces and Government Interventions for Business Leaders
- Unit 10 Customer Relationship Management Assignment – CRM Processes & Stakeholder Roles
- CIPD 7HR02 Resourcing and Talent Management to Sustain Success
- Athe Level 3 Health and Social Care Assessment Questions
- M/618/4168 Unit 2 Principles, Values and Regulation in the Health and Social Care Sector – ATHE Level 3
- ILM Communication Skills Self-Assessment
- ILM Unit 8600-309: Understand How to Establish an Effective Team
- CMI Unit 525 Using Reflective Practice to Inform Personal and Professional Development
- Understand and Work with a Wide Range of Stakeholders and Organisational Structures – Assignment 1
- Assessment: Financial Performance Evaluation of Savory Snacks Company Ltd for Credit
- CMI L5 Assignment: Managing Stakeholder Relationships: Strategies, Challenges, and Best Practices
- Level 3 Unit 2 Assignment: Principles, Values and Regulation in the Health and Social Care Sector
- COM4006 Assignment: Introduction to Academic Skills and Professional Development
- Assessment: Managing Organisational Change: Evaluating Strategies, Challenges, and Impact
- UNIT CMI 706 Assignment: Finance for Strategic Leaders: The Role, Scope, and Impact of Finance
- ENGINEERING DESIGN TMA2 v1: CAD Design Report: Specification, Evaluation & Drawings
- Unit CMI 514 Assignment: Analysis of Organisational Change: Managing Change
- EMS402U TMA1: Engineering Design Solutions: Concept Development & Assessment
Fuzz testing using Web Applications And Design and development of a fuzzer: Secure Systems Development Assignment, MMU, UK
| University | Manchester Metropolitan University (MMU) |
Part 1: Fuzz testing using Web Applications
Part2: Design and development of a fuzzer
Part 1:
We are using Kali Linux distribution for this part. An online OS is available here:
A web application like WFuzz can be found in the Web Application Analysis section of the Kali Linux menu. Wizz is a command-line utility included in Kali Linux. It is used to discover common vulnerabilities in web applications through the method of fuzzing. Fuzzing is the concept of trying many known vulnerable inputs with a web application to determine if any of the inputs compromise the web application. It is a great tool to be able to quickly check common vulnerabilities against an application. It is also valuable for testing previously reported vulnerabilities to ensure that regressions don’t occur in an application.
1. A payload to test against the target application
2. The parameter to inject the payload into
3. The target application URL
In addition to this, we often need to provide a cookie to fuzz for it to properly reach the vulnerable component. This is done by adding the -b argument. This is required if you need to authenticate to get to the section of the application you wish to attack.
Do You Need Assignment of This Question
To understand how to fuzz can be used, suppose that we have a login page that uses SQL to query if the user provides a valid username or password. When we submit the login form, the form will post the username and password as parameters. If the username and password is valid, the user is sent to a welcome page. In all other cases, they will get an error saying invalid username or password.
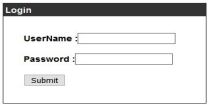
With login forms like this, we often want to check for the possibility of SQL injection. This is a task that fuzz would be perfect for. To start, we need to determine how the data is sent to the backend when it is submitted by the user. To do this, we can use a tool like Burp Suite to intercept the packet sent when the submit button is pressed. Doing this will show us how the post data is formatted.
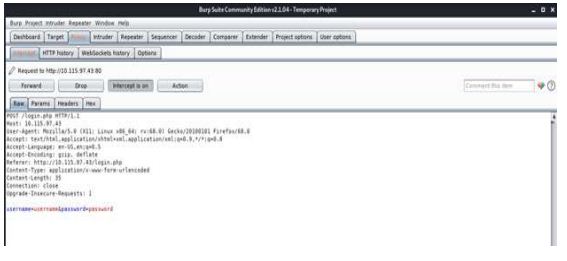
From this intercept, we can see that data is passed to the server in the format
“username=input&password=input”. We can tell fuzz to send data in this format, and it will successfully be able to send post requests to the login page. To do this, we can use the command:
Buy Answer of This Assessment & Raise Your Grades
To break down this command, we can take a look at what each argument provides to fuzz. To start, the flag -c makes the output of the terminal color, which just makes the results easier to read. The flag -z specifies the payload to use to fuzz the webpage. The argument provided is a file, which is located at
/usr/share/wordlists/wfuzz/Injections/SQL.txt. Kali Linux keeps all the wordlists for each program in /usr/share/wordlists. Inside the fuzz folder, you will find all the common wordlists that fuzz is set up to use. In this case, I’ve used the SQL injection wordlist to look at common SQL injections. You can just as easily add to these lists or create your own if you have specific test cases you want to apply.
After this, we use the -d flag to specify what data to post to the server. As we discussed, the format is “username=INPUT&password=INPUT”. In this case, I set the username to admin and set the password to FUZZ. Wfuzz is set up to replace the keyword FUZZ with the words within the provided payload file, so in this example, we are injecting SQL injection keywords into the password parameter. Finally, we supply the target URL and run the application. Once this is done, we will get an output, similar to what is shown below.
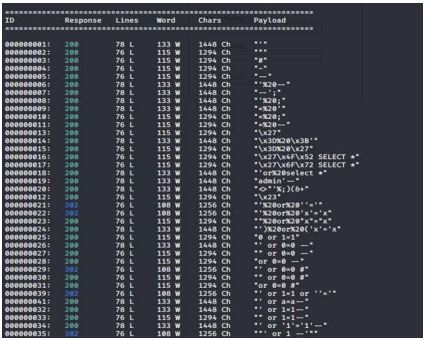
Part 2: To make software or systems crash or break through their defenses, fuzz testing often includes entering huge volumes of random data, known as fuzz, into the software or system being tested. If a vulnerability is discovered, a fuzzer software program can be used to determine the root cause.
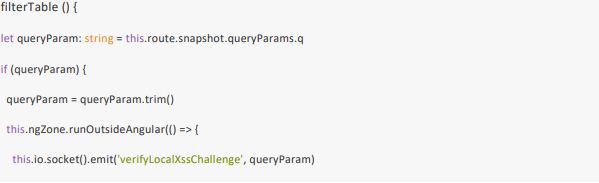
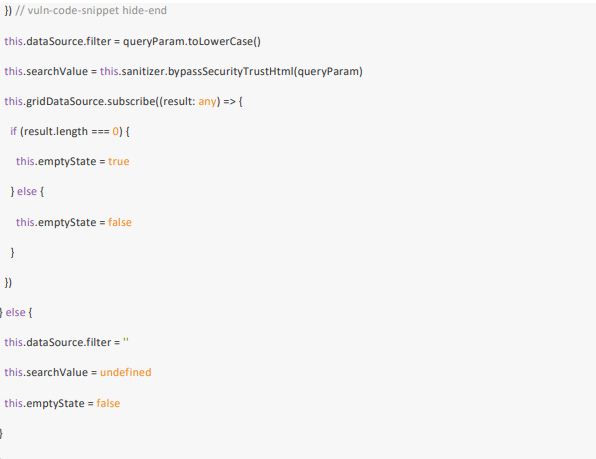
Use the example above to design and develop a fuzzy that will identify the weaknesses and supply some code fix options. Provide a technical note that includes the following:
1. Design and development of the fuzzer
2. Automatic Detection of the code weaknesses
3. Discussion on the impact of the weaknesses identified
4. Research a vulnerable application in Exploit DB1 search and pick the exploits, which have that respective application available for download, and reproduce the exploit by using a fuzzer of your choice.
Are You Looking for Answer of This Assignment or Essay
Diploma Assignment Help UK provides high-quality TEFL diploma assignment help to students in the UK. We have a team of experienced TEFL tutors who are familiar with the TEFL curriculum and can provide expert guidance on how to complete your assignments. In addition, we offer a wide range of resources that can help you research and write your assignments, including TEFL textbooks, journal articles, and online course materials. With our assignment help UK, you can be confident that you will receive the grades you deserve.



